
Here is a list of the top-level country domains.
Responses can be authoritative, coming from an authoritative server, or not,
coming from a caching server.
They can also be truncated, which means that not all
of the information available from the server fits in the 512 byte limit.
Resource records can be
Responses also provide a time for which the data is to be trusted (the Time-To-Live). If a domain name does not exist, the response is NXDOMAIN: non-existant domain.
Primary and secondary servers can also be caching servers for zones for which they are not authoritative.
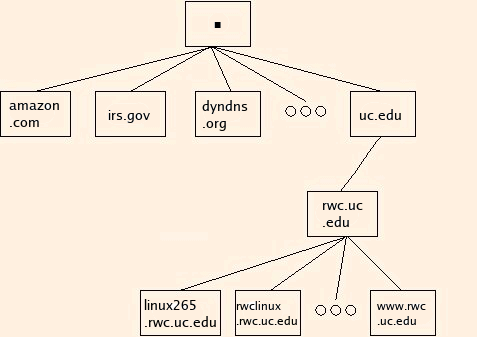
For instance, if the local domain is "lab265" and the search domains are "rwc.uc.edu" and "uc.edu", the lookup of "mickey.mouse" would involve queries for:
Note that a search for "mickey.mouse." would only involve the first lookup.
The use of search domains is discouraged, since it can result in excessive waits for DNS lookups.
97.122.137.129.in-addr.arpaYou can also perform this query using dig -x 129.137.122.97 (dig is a souped-up version of NSLOOKUP in Windows).
Do the last one from multiple PCs and cross check the results. What do you notice about the order of the resource records in the answer and authority sections? (See question 3 in the Question and Answer chapter of the DNS HOWTO.)
dig @server-ip -t AXFR domain can be used to test access through TCP after we reconfigure named.
Recall from our discussion in weeks 1, 2 and 5 that in our distribution, there are two copies of inittab: one on the root filesystem, and one on the /var filesystem, and that these two must agree. Changing the one in /var is easy; to change the one on /:
- mount --bind / /mnt
- mount -wo remount /mnt
- sed -i /mnt/etc/inittab -e 's/3:initdef/4:initdef/'
- umount /mnt
The first mount allows you to access the partition containing the root partition at /mnt, without the links to /var. The second mount allows you to write to the root partition at /mnt (it does not affect the read-only mount at /). The sed changes the default runlevel from 3 to 4, and the final umount removes our access to the root partition through /mnt.
©2015, Kenneth R. Koehler. All Rights Reserved. This document may be freely reproduced provided that this copyright notice is included.
Please send comments or suggestions to the author.