Notes for Week 13
-
First, a picture, and some names and acronyms:
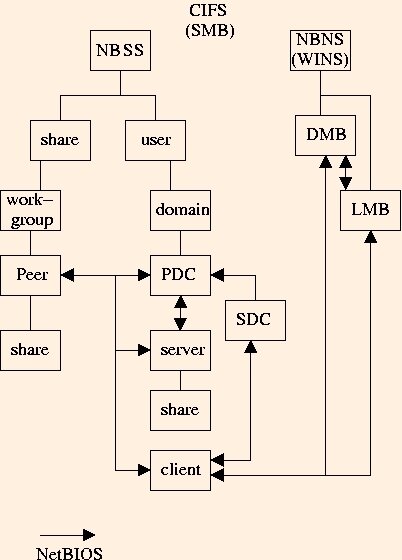
- ACE - Access Control Entry - contains SID and access rights
- ACL - Access Control List - list of ACEs for an object
- CIFS - Common Internet File System - Microsoft's name for their Windows network file system
structure, also known as SMB
- DC - Domain Controller (PDC or SDC)
- deny modes - specified when a client opens a file, telling server what other types of access
are allowed while this client has the file open (may deny none, read, write, all)
- DMB - Domain Master Browser - coordinates browse lists across domains
- Domain (or NT Domain) - a group of PCs which need only log in to the PDC in order to access any service
in the domain
- FID - file identifier
- IPC$ - InterProgram Communications share provided by servers - used for connections to named pipes
- IPX - Internetwork Packet eXchange - Novell's network protocol
- LMB - Local Master Browser - local WINS server for browse requests
- lock - request by a client to prevent other clients from reading and/or writing to all or a
section of a file
- machine name - NetBIOS name for a PC
- NBNS - NetBIOS Name Service - another name for WINS
- NBSS - NetBIOS Session Service - SMB client/server protocol
- NCP - Netware Core Protocol, or Netware Control Program (Novell)
- NetBIOS - Network Basic Input Output System - first version of SMB - not routable; NetBIOS over TCP/IP
(or UDP) is routable and is standard network/transport layer used by SMB; NetBIOS may also ride on
IPX and DECnet
- NetBIOS name - name of clent for SMB purposes - not necessarily related to DNS names
- NetBEUI - NetBIOS Enhanced User Interface - routable version of NetBIOS
- nmbd - WINS daemon, providing NetBIOS name advertising (DMB) and resolution on UNIX
- oplock - opportunistic lock - only circumstance when a server sends an unsolicited message to a client
(when two clients request oplocks which are incompatible, first will be broken)
- PDC - Primary Domain Controller - provides authentication services for multiple CIFS servers
- Redirector - that part of client which interfaces local file and print requests to server
- SAM - Security Access Manager (used by DCs for authentication)
- Samba - SMB implementation for UNIX
- SDC - Secondary Domain Controller - backup to PDC
- share - a directory (sub-)tree or printer provided by a server
- share level security - client only needs to supply a password for the share
- SID - Security Identifier - user or group id
- SMB - Server Message Block (see CIFS) - roughly analogous to Netware NCP
- smbd - SMB daemon, providing CIFS file and print services from UNIX; also handles share and user mode
authentication
- smbfs - SMB file system, supported directly by Linux kernel code
- TID - tree (path) identifier provided upon connection to share
- UID - user identifier provided upon authentication - must accompany all requests to share
- user level security - each client must be authenticated by server
- WINS - Windows Internet Name Service
- workgroup - each PC in workgroup does its own authentication for shares it provides
-
Client can send SMBs to:
- connect to / disconnect from file and print shares
- open / close (print) files
- read / write file
- create / delete files, directories
- search directory
- get / set file attributes
- lock / unlock ranges of bytes in files
- Access rights (part of ACE) include
- file_read_data (r--)
- file_list_directory (r-x)
- file_write_data (-w-)
- file_add_file (to directory) (-w-)
- file_add_subdirectory (to directory) (-w-)
- file_execute (--x)
- file_delete_child (file or subdir in directory) (-w-)
- file_read_attributes (r-x for directory)
- file_write_attributes (-w- for directory)
There are many others.
Samba does not grant more access than the UNIX host allows through permissions.
UNIX "other" permissions map into the NT group EVERYONE.
-
NetBIOS Names
-
name of computer, 15 characters long (padded with spaces), uppercase
-
16th character is the NetBIOS suffix:
| hex value | Meaning |
|---|
| 00 | workstation redirector |
| 03 | messenger service |
| 1B | DMB |
| 1C | DC |
| 1D | LMB |
| 1E | browser elections |
| 20 | file server |
There are many others.
-
full format is
\\netbiosname\sharename
-
Clients keep NetBIOS names in cache for 10-15 minutes.
-
On an NT-based system (NT, 2000, XP), static NetBIOS name to IP address mappings are in
C:\WINNT\SYSTEM32\DRIVERS\ETC\LMHOSTS
-
print$ is the share name for downloading printer drivers
- To enable printer sharing with CUPS, it would be necessary to
ln -sf /usr/bin/smbspool /usr/lib/cups/backend/smb
-
EXERCISES for Week 13:
-
Add firewall rules to permit both TCP and UDP access to ports 137-139 and 445. Examine the tail of the system log file
for samba-related entries.
-
Add a user test by executing useradd test && smbpasswd -a test.
The test user's Samba password should also be "test". Do not give the test user a UNIX password.
-
Test samba by executing smbclient -U test -L your-IP-address, both from your PC and from another.
-
Typical SMB Protocol Sequences (this assumes the client is 9x, but the general pattern is the same for later versions of Windows):
- On startup, clients send their NetBIOS names & IP addresses to WINS server (via UDP).
- If there is no WINS server, all NetBIOS name resolution is done by UDP broadcast (which
isolates name resolution to the local sub-net).
- Workgroup computers hold an election every 11-15 minutes to determine who is LMB - it keeps a list of available
services for browsing by other computers; election criteria include longest uptime, most senior protocol version;
LMB provides list that appears when you open Network
Neighborhood.
- Hosts announce their NetBIOS names periodically.
- LMB locates its DMB using WINS to provide domain-wide browse lists; propagation of changes
can take more than an hour for remote subnets.
- Client requests a list of PDC / SDCs - sends a netlogon SMB to each of them; first to reply
is the one used.
- Client sends negprot SMB to negotiate protocol variants with server (what client understands).
- Client sends sesssetupX SMB to logon and receive UID.
- Client sends tcon or tconX SMB to specify share it wants to connect to, and to receive
TID.
- Client issues NetWkstaUserLogon to get name of logon script.
- Client connects to NetLogon share to retrieve logon script (and then disconnects).
- Client sends NetUserGetInfo to find home share name.
- Client connects to home share and gets profiles (and then disconnects).
- Client reconnects to NetLogon to get policies.
- Windows clients drop network mappings that have been idle for 10 minutes or longer; connections are
reestablished using cached passwords.
Protocol usage varies with dialect (ie., Windows version). Since XP, cached passwords are no longer used.
Use wireshark to observe packets as Windows is booted on your partner's PC. How much traffic occurs on the SMB ports?
Some advice on using wireshark:
- Add yourself to the wireshark group. This will not appear to take effect until the next time you login; until then, you can issue the
command newgrp wireshark to start a new shell as a member of the group. Be sure to exit when you are done.
- Change the web browser command in "Edit/Preferences" from "mozilla %s" to seamonkey %s.
- To start a capture, under "Capture/Options", check an interface and push the Start button.
- To only capture SMB packets, use the capture filter port 137 or 138 or 139 or 445.
- To capture those ports on only one host, preprend that filter with host ip-address and, and enclose the port part in parentheses.
- Push the red button to stop capturing.
- Click on a packet in the top frame to examine it.
- Click on a right-pointing triangle in the middle frame to display details.
©2015, Kenneth R. Koehler. All Rights Reserved. This document may be freely reproduced provided that this copyright notice is included.
Please send comments or suggestions to the author.
